
Menu
Our services include:
We provide a full spectrum of IT service designed to help businesses operate efficiently, securely, and with the latest technological advancements.
Ensures that physical and virtual infrastructures are secure from threats, vulnerabilities, and attacks, both on-premises and in cloud environments.
Safeguards the development, deployment, and use of software applications, ensuring that vulnerabilities are minimized, and secure coding practices are enforced.
Encompasses governance, risk management, compliance, and the overall security culture of an organization to protect data, processes, and resources.
wift and effective
assessment of IT security.
wift and effective
assessment of IT security.
Ensure 24/7 security with hands-on user training for cyber- attack response protocols.
At SecureiTrust, we adopt a holistic Security 360° approach, integrating protection across multiple layers of your business operations. Our methodology combines proactive defense, real-time threat detection & prevention, and rapid response, addressing risks before they impact your business.
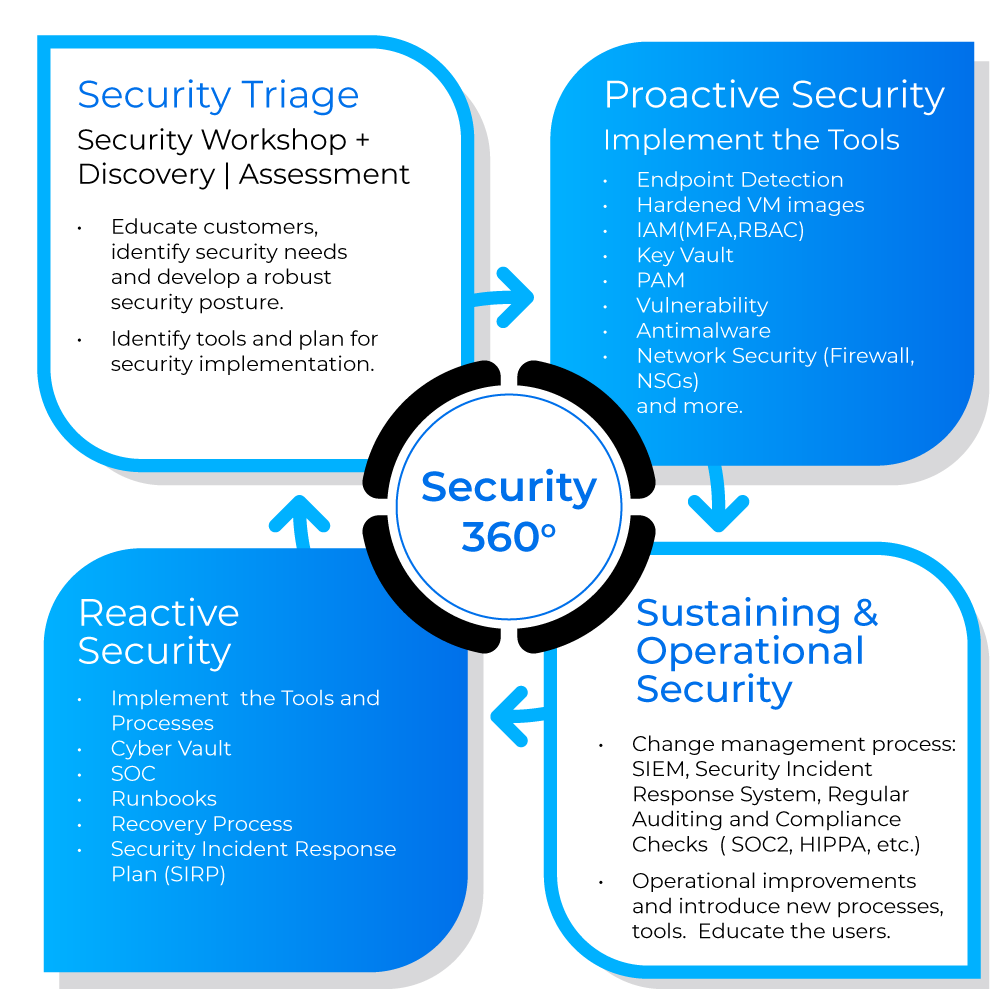
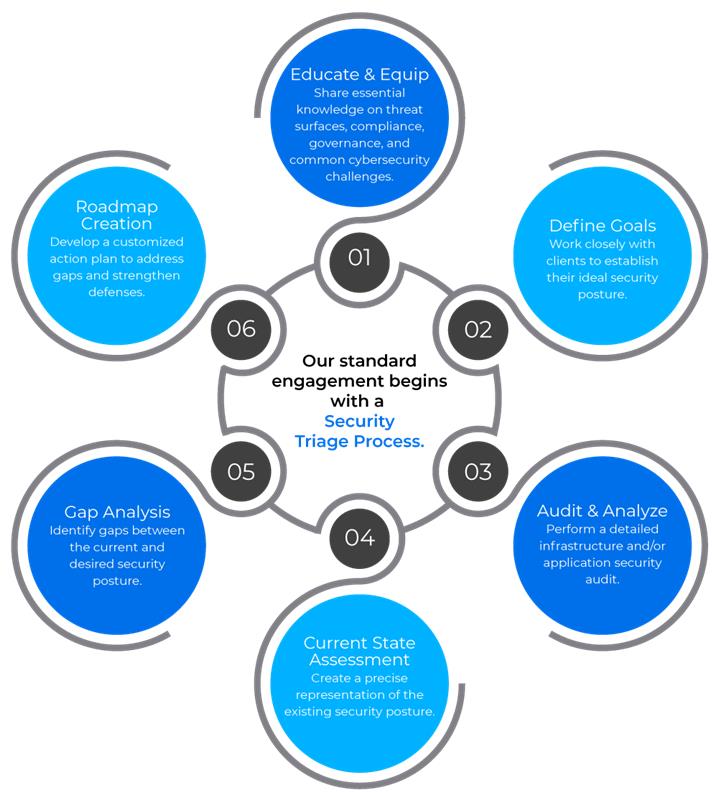
Every business has unique cybersecurity needs. To address these effectively, a SecureiTrust team member engages with your IT team to gather critical insights. These inputs are then analyzed by our Security Triage Analyst, who creates a clear and actionable path forward, following a Security Triage Process.
Each solution is meticulously customized to meet the client’s specific needs and industry demands, while adhering to budgetary considerations.

SECUREi TRUST is a leader in digital security solutions, offering robust infrastructure services, cloud data management, and comprehensive organizational security.
Copyright © 2024 All Right Reserved By SECUREi TRUST.